hello fellow rcloners,
as discussed https://forum.rclone.org/t/rclone-1-5-6-windows-finds-trojan-win32-cryptinject-msr/26172/33, windows defender considers rclone.exe to be a virus.
for most rcloners, item 1. will suffice.
i work on many computers/servers and always copy a set of files to each machine.
often have to copy additional files.
there are many files in there that anti-virus scanners will freak out about.
in addition, i also work on several of the free, awesome windows server 2019 hyper-v edition, which has no gui, no control panel, no settings, no windows explorer. as a result, whitelisting an every changing set of files is a real pain.
so for that use-case i use, item 2. and/or item 3.
this is a short guide with three workarounds.
- whitelist the threat using windows defender, three ways, from least secure to most secure
a. whitelist all files of typeTrojan:WIn32/CryptInject!MSRon the entire file system.
b. whitelist the folder containing rclone.exe
c. whitelist just one instance of rclone.exe - modify the rclone.exe - changing a single byte and as a result change the hash.
- upx the rclone.exe - which will compress rclone.exe and as a result, change the hash
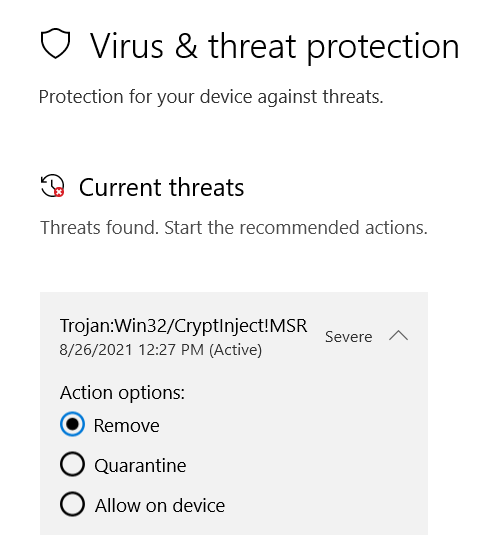
1a. whitelist all files of type Trojan:WIn32/CryptInject!MSR on anywhere on the file system.
---press the windows key or click the windows icon
--- type 'antivirus' + enter or click 'Virus & threat protection'
--- click 'allow on device'
--- click 'start actions'
1b. whitelist the folder containing rclone.exe
---press the windows key or click the windows icon
--- type 'antivirus' + enter or click 'Virus & threat protection'
--- click 'manage settings'
--- click 'start actions'
--- click 'add or remove exclusions`
--- click 'add an exclusion'
--- click 'folder'
--- choose the path and click 'select folder'
1c. whitelist just one instance of rclone.exe
---press the windows key or click the windows icon
--- type antivirus + enter or click 'Virus & threat protection'
--- click 'manage settings'
--- click 'start actions'
--- click 'add or remove exclusions'
--- click 'add an exclusion'
--- click 'file'
--- navigate to the rclone.exe and click open'
- modify the rclone.exe - changing a single byte and as a result change the hash.
@ivandeex here expressed concern with this technique and so far seems to be working.
there are many ways to modify a file, i used notepad++.
--- copy rclone.exe to rclone.byte.exe
--- open rclone.byte.exe in notepad++
--- near the top of the file, findThis program cannot be run in DOS mode
--- change it to 'This program cannot be run in DXS mode'
--- save the file
![]()
![]()
- upx the rclone.exe - which will compress rclone.exe and as a result, change the hash
upx is a program that compresses an executable file and as a result change its hash.
as a side benefit rclone.exe will shrink from42.6 MBto11.8 MB
note: this a very small delay when starting the compressed version.
---download upx from https://github.com/upx/upx/releases/tag/v3.96
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>copy rclone.exe rclone.upx.exe
1 file(s) copied.
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>upx rclone.upx.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX 3.96w Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
File size Ratio Format Name
-------------------- ------ ----------- -----------
44692992 -> 12425728 27.80% win64/pe rclone.upx.exe Packed 1 file.
and here are the results.
i placed each modified rclone.exe into its own folder and made sure the filename is `rclone.exe
C:\data\rclone\scripts\exe>rclone version
The system cannot execute the specified program.
C:\data\rclone\scripts\exe>.\byte\rclone.exe --version
rclone v1.56.0
- os/version: Microsoft Windows 10 Pro 2009 (64 bit)
- os/kernel: 10.0.19043.1165 (x86_64)
- os/type: windows
- os/arch: amd64
- go/version: go1.16.5
- go/linking: dynamic
- go/tags: cmount
C:\data\rclone\scripts\exe>.\upx\rclone.exe --version
rclone v1.56.0
- os/version: Microsoft Windows 10 Pro 2009 (64 bit)
- os/kernel: 10.0.19043.1165 (x86_64)
- os/type: windows
- os/arch: amd64
- go/version: go1.16.5
- go/linking: dynamic
- go/tags: cmount
C:\data\rclone\scripts\exe>.\byte\rclone.exe config reconnect
Usage:
rclone config reconnect remote: [flags]
Flags:
-h, --help help for reconnect
Use "rclone [command] --help" for more information about a command.
Use "rclone help flags" for to see the global flags.
Use "rclone help backends" for a list of supported services.
Command reconnect needs 1 arguments minimum: you provided 0 non flag arguments: []
C:\data\rclone\scripts\exe>.\upx\rclone.exe config reconnect
Usage:
rclone config reconnect remote: [flags]
Flags:
-h, --help help for reconnect
Use "rclone [command] --help" for more information about a command.
Use "rclone help flags" for to see the global flags.
Use "rclone help backends" for a list of supported services.
Command reconnect needs 1 arguments minimum: you provided 0 non flag arguments: []