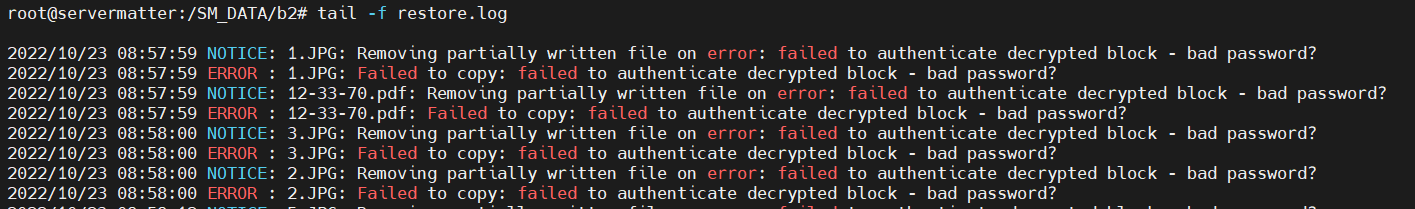
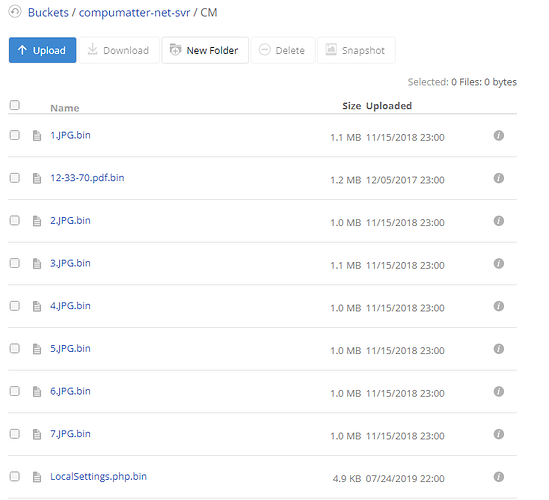
What is the problem you are having with rclone?
Server drives toasted. Cannot figure out how to restore previously encrypted files to get going again. Trying to use the "copy" command to retrieve the files from a specific Backblaze bucket (compumatter-net-svr) to our new server.
If we try the rclone copy one way, it ends up download everything but they are encrypted "bin" files. If we change which rclone conf section is being referenced, it throws the error shown below. We are in an emergency state and feel confident we have the correct passwords and salt
Run the command 'rclone version' and share the full output of the command.
'''
rclone v1.60.0
- os/version: ubuntu 22.04 (64 bit)
- os/kernel: 5.15.0-50-generic (x86_64)
- os/type: linux
- os/arch: amd64
- go/version: go1.19.2
- go/linking: static
- go/tags: none
'''
Which cloud storage system are you using? (eg Google Drive)
Backblaze
The command you were trying to run (eg rclone copy /tmp remote:tmp)
rclone copy --log-file=restore.log --log-level DEBUG --low-level-retries 20 --tpslimit 10 --exclude-from rclone.excludes --config=rclone-114.conf data-drive-crypt:"" "/SM_DATA/b2/114-restore""
The rclone config contents with secrets removed.
# file rclone-114.conf
[data-drive-crypt]
type = crypt
password2 = rxBY3MlvDnRjoaqIe.....
remote = data-drive:compumatter-net-svr
directory_name_encryption = true
filename_encryption = standard
password = kaEhhykCK5tJahXbkTof7C....
[data-drive]
type = b2
account = 34e3d.....
key = 001b8e1f43569822a892.....
A log from the command with the -vv flag
2022/10/22 20:06:49 INFO : Starting transaction limiter: max 10 transactions/s with burst 1
2022/10/22 20:06:49 DEBUG : rclone: Version "v1.60.0" starting with parameters ["rclone" "copy" "-vv" "--log-file=restore.log" "--low-level-retries" "20" "--tpslimit" "10" "--exclude-from" "rclone.excludes" "--config=rclone-114.conf" "data-drive-crypt:" "/SM_DATA/b2/114-restore"]
2022/10/22 20:06:49 DEBUG : Creating backend with remote "data-drive-crypt:"
2022/10/22 20:06:49 DEBUG : Using config file from "/SM_DATA/b2/rclone-114.conf"
2022/10/22 20:06:49 DEBUG : Creating backend with remote "data-drive:compumatter-net-svr"
2022/10/22 20:06:50 DEBUG : Creating backend with remote "/SM_DATA/b2/114-restore"
2022/10/22 20:06:53 DEBUG : CM: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : bin: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : boot: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : build: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : cm-sav: Skipping undecryptable dir name: illegal base32 data at input byte 2
2022/10/22 20:06:53 DEBUG : cm: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : dev: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : etc: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : home: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : lib: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : lost+found: Skipping undecryptable dir name: illegal base32 data at input byte 4
2022/10/22 20:06:53 DEBUG : media: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : netdata-updater.log.0iVaxu.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.1MZmwv.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.5YY2lE.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.9RtyKk.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.9fWYuD.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.DMzsaD.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.LFSzbP.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.Rrl3Gu.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.XUhJNk.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.ZzOfzX.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.t0fS8j.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.wORKho.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : netdata-updater.log.xhNv9Z.bin: Skipping undecryptable file name: illegal base32 data at input byte 7
2022/10/22 20:06:53 DEBUG : opt: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : proc: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : root: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : run: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : sbin: Skipping undecryptable dir name: not a multiple of blocksize
2022/10/22 20:06:53 DEBUG : srv: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : sys: Skipping undecryptable dir name: illegal base32 data at input byte 1
2022/10/22 20:06:53 DEBUG : tmp: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : usr: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : var: Skipping undecryptable dir name: illegal base32 data at input byte 3
2022/10/22 20:06:53 DEBUG : Local file system at /SM_DATA/b2/114-restore: Waiting for checks to finish
2022/10/22 20:06:53 DEBUG : Local file system at /SM_DATA/b2/114-restore: Waiting for transfers to finish
2022/10/22 20:06:53 INFO : There was nothing to transfer
2022/10/22 20:06:53 INFO :
Transferred: 0 B / 0 B, -, 0 B/s, ETA -
Elapsed time: 4.0s
2022/10/22 20:06:53 DEBUG : 7 go routines active