Confirmed on Windows Server 2019 instances in AWS's EC2. The rclone executable actually disappears in my case.
it has been quarantined, just need to whitelist it.
if you a using a non-GUI version of windows, like hyper-v edition, dealing with anti-virus can be a huge pain.
as a workaround. sometimes it is enough to modify a single byte
i often do that with certain .exe
for example,
- change
This program cannot be run in DOS modetoThis program cannot be run in xxx mode - change the file name.
Not sure that will work. I found this signature in my defender definitions:
OFN:rclone.exe
rclone config reconnect
RCLONE
github.com/rclone/rclone/cmd
github.com/rclone/rclone/vfs
There are also behavioural signatures for rclone as well as other file synchronization tools like MEGAsync and FreeFileSync. It seems they are really afraid of data exfiltration.
I don't use Windows but I was wondering the same thing. On my mac, I copied the rclone executable and added a single null byte. It seems to work fine and, as expected, changes the checksums. Still, not a great workaround but it's an option
need to find a workaround, as i install rclone on many computers, many using not-GUI versions such as hyper-v edition, whitelisting apps is a pain. windows defender hates nirsoft.
just triggered a windows update and it downloaded the latest definitions.
did some quick testing
- rclone.exe - windows blocked it
- change a single byte, windows did not block it.
This program cannot be run in DOS modetoThis program cannot be run in xxx mode - upx the rclone.exe, windows did not block it
C:\data\rclone\scripts\exe\rclone-v1.56.0-windows-amd64>rclone.exe version
The system cannot execute the specified program.
C:\data\rclone\scripts\exe\rclone-v1.56.0-windows-amd64>rclone.byte version
rclone v1.56.0
- os/version: Microsoft Windows 10 Pro 2009 (64 bit)
- os/kernel: 10.0.19043.1165 (x86_64)
- os/type: windows
- os/arch: amd64
- go/version: go1.16.5
- go/linking: dynamic
- go/tags: cmount
C:\data\rclone\scripts\exe\rclone-v1.56.0-windows-amd64>rclone.upx.exe version
rclone v1.56.0
- os/version: Microsoft Windows 10 Pro 2009 (64 bit)
- os/kernel: 10.0.19043.1165 (x86_64)
- os/type: windows
- os/arch: amd64
- go/version: go1.16.5
- go/linking: dynamic
- go/tags: cmount
C:\data\rclone\scripts\exe\rclone-v1.56.0-windows-amd64>rclone.byte.exe config reconnect
Usage:
rclone config reconnect remote: [flags]
Flags:
-h, --help help for reconnect
Use "rclone [command] --help" for more information about a command.
Use "rclone help flags" for to see the global flags.
Use "rclone help backends" for a list of supported services.
Command reconnect needs 1 arguments minimum: you provided 0 non flag arguments: []
C:\data\rclone\scripts\exe\rclone-v1.56.0-windows-amd64>rclone.upx.exe config reconnect
Usage:
rclone config reconnect remote: [flags]
Flags:
-h, --help help for reconnect
Use "rclone [command] --help" for more information about a command.
Use "rclone help flags" for to see the global flags.
Use "rclone help backends" for a list of supported services.
Command reconnect needs 1 arguments minimum: you provided 0 non flag arguments: []
Not good, sounds like FBI and Microsoft could be doing some widespread damage control in a situation where they are (currently) unable to find/stop all the compromised devices. PrintNightmare?
how about rclone selfupdate nightmare.
C:\data\rclone\scripts\exe\rclone-v1.55.1-windows-amd64>rclone selfupdate
Successfully updated rclone from version v1.55.1 to version v1.56.0
C:\data\rclone\scripts\exe\rclone-v1.55.1-windows-amd64>rclone version
'rclone' is not recognized as an internal or external command,
operable program or batch file.
I'm on Server 2016, latest Defender version and definition, Rclone 1.57.0-beta.5642, non-exempt. No issues here.
This worked for me, thank you!
I'm on 1.347.472.0 now. Still nothing. Perhaps the newer 1.57 beta doesn't trigger?
now using 1.347.472.0 and v1.57 beta.
i think you are correct, that does not trigger windows defender.
VirusTotal only has MS flagging the file. Looks like I'm too new a user to post more than one image :-/
Check Point Threat Emulation (0-day sandbox emulation) did not find anything:
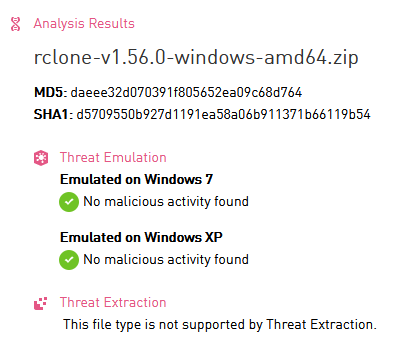
Still leaves you a bit nervous...
to all fellow rcloners, i have create a short howto guide to workaround the issue.
https://forum.rclone.org/t/rclone-exe-is-a-virus-workarounds/26223
- whitelist the threat using windows defender, three ways, listed from least secure to most secure
- modify the rclone.exe - changing a single byte and as a result change the hash.
- upx the rclone.exe - which will compress rclone.exe and as a result, change the hash
I'm simply getting Access is denied. and exit code 5:
C:\Temp> rclone version
Access is denied.
C:\Temp> echo %ERRORLEVEL%
5
This is when trying to run rclone version 1.56. Rclone version 1.55 works just fine. Changing the hash of rclone.exe version 1.56 "fixes" it (echo 0 >> rclone.exe).
So it appears to be the same issue, although on this computer I'm not using Windows Defender, but Symantec Endpoint Protection for "Virus & threat protection". Strangely enough it does not report any issues with the exe, and I can't find anything relevant in the logs, neither in Windows event logs. Only the "Access is denied." when trying to execute it.
hi, for windows defender, that does not seem to work
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>copy rclone.exe rclone.echo.exe
1 file(s) copied.
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>rclone.exe hashsum md5 . --include=rclone*.exe
2021/08/28 12:22:22 NOTICE: Config file "C:\\Users\\user01\\AppData\\Roaming\\rclone\\rclone.conf" not found - using defaults
41f79eac62a4d211b18556e93fc5a258 rclone.upx.exe
c7291c9b893dbec2ffd0f0247512f928 rclone.byte.exe
0a7e53b6b6d17d38cc6ae8cda179d186 rclone.exe
0a7e53b6b6d17d38cc6ae8cda179d186 rclone.echo.exe
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>echo 0 1>>rclone.echo.exe
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>rclone.exe hashsum md5 . --include=rclone*.exe
2021/08/28 12:22:22 NOTICE: Config file "C:\\Users\\user01\\AppData\\Roaming\\rclone\\rclone.conf" not found - using defaults
41f79eac62a4d211b18556e93fc5a258 rclone.upx.exe
c7291c9b893dbec2ffd0f0247512f928 rclone.byte.exe
0a7e53b6b6d17d38cc6ae8cda179d186 rclone.exe
0b72c426ffa2bcbe09604eee77700b39 rclone.echo.exe
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>copy rclone*.exe C:\data\rclone\scripts\exe
rclone.byte.exe
rclone.echo.exe
rclone.exe
rclone.upx.exe
4 file(s) copied.
d:\data\rclone\exe\rclone-v1.56.0-windows-amd64>cd /d C:\data\rclone\scripts\exe\
C:\data\rclone\scripts\exe>rclone.echo.exe version
The system cannot execute the specified program.
C:\data\rclone\scripts\exe>rclone.byte.exe version
rclone v1.56.0
- os/version: Microsoft Windows 10 Pro 2009 (64 bit)
- os/kernel: 10.0.19043.1165 (x86_64)
- os/type: windows
- os/arch: amd64
- go/version: go1.16.5
- go/linking: dynamic
- go/tags: cmount
I think you meant to tag me on that post, but somehow I got pinged anyway. In any case, more workarounds are always good.
I've also tested the beta versions trick since it seems to be the easiest, and the commit immediately after v1.56.0 only changes a log level, so that's what I'll be using.
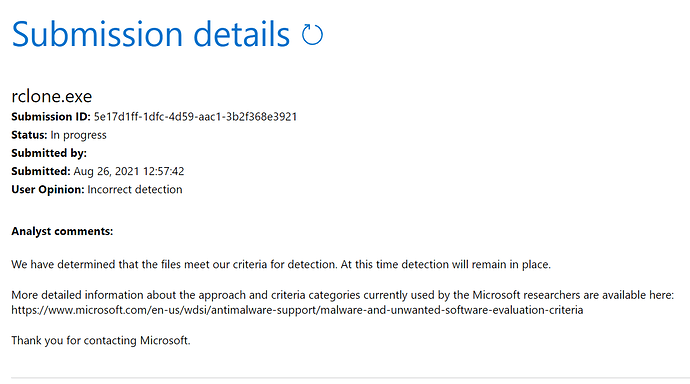
I've filed a dispute on the previous rejection from Microsoft, btw. Maybe they'll listen this time.
Strange.. Regardless, I'm not very fond of editing the binary like that and use it for "production". In my case it was just as a proof of concept. Would rather use UPX as you've described, but doesn't some security tools warn or block anything upx compressed? Using the beta version is a good alternative, I think. Personally I will just use my own build from source, since I do that anyway.
well, in your case, you have a inside view of rclone and can choose a stable beta version.
in my case, never use beta software.
in fact, i try to stay on step behind, still using v1.55.1
for the rest of us, that trick will require always using an unstable beta.
new bugs on existing features can sneak in, such as the current issue with --daemon
i believe this problem will not go away, too many hacker tools are using rclone and that will increase.
microsoft and other anti-virus providers have zero incentive to whitelist rclone.exe
for most rcloners, simply whitelisting will be a good enough solution.
for others, who use rclone on many machines for critical backups, having a bunch of those backups fail at any time, and all at the same time, is a nightmare that needs better solutions.
having a .exe disappear really messes with workflows...
so far, my workarounds are still working.